Current mission: update the SoyBooru tag dictionary by clicking the ? button next to tags, inserting the TagDefinition template, and filling it in.
The Ultimate Doxing Guide

|
The following media may only be utilized upon its ratification by President Quote when the end times are approaching Find a nuclear bunker ₦Ø₩ |
 |
You can read this for more info about the topic |
 |
|---|
This doxing guide has everything you need to know to dox someone. You along with knowledge need some IQ to create plans, collect some info to do a certain thing, and etc. This means 'p spammers can't dox. This page also doesn't go over shit nobody cares about.
Stay safe[edit | edit source]
Main article: OPSEC
Before you start taking revenge on the literal who discord pedophile and accidentally stumble into a honeypot and end up having Kolyma agents knocking on your door, do these to stay safe:
- You WILL use Tor (download here) when doing these (ironically it was created by the US Navy but it's safe (hopefully))
- You WILL read the darknet bible (Tor required)
- You WILL wear a mask[Marge...]
- Remember glowies aren't a joke
- You WILL NOT go to sites you're not sure of
- You WILL use a VPN
- You WILL NOT use email to communicate with others on the dark web unless you are using PGP encryption. Only use peer-to-peer-messaging apps with a user privacy policy such as SimpleX Chat to communicate. By the way, anonymity and privacy are two different things. Privacy means that they know who you are, but they don't know what you're doing. Anonymity is when they don't know who you are, but they know what you're doing. You obviously want a mix of these two.
Suggested 'oxxing procedure[edit | edit source]
So - you found a tranny that makes futa cock vore cub rape porn online or something. Wat nou? A helpful procedure for newGODS is outlined below.
- CHIVE. CHIVE. CHIVE.
- The importance of this step cannot be understated, but it is sadly often overlooked. Yeah, it's boring, we know. Don't be a SLF and turn it into a faildox cause you couldn't be bothered. 'chiving tools can be found in the links section.
- Always assume there will be snitches monitoring - if a target is alerted before you can 'chive, all evidence could be lost
- Datamine - Gather usernames, accounts, images (including an eye-catching thumbnail for /raid/), search breach sites, phonebooks, etc... Refer to below sections for tools and methods.
- Work backwards - In order to confirm that you've found your target, start with the last piece of information you found and try to work your way back to the information you started with. If it checks out, proceed. If not, go back to (2.) and see if there are any other people your target might be.
- Windox? (full name, address, email, phone, relatives (including contact details), place of work)? If yes, go to (8.), else continue.
- Deploy to /raid/
- Create a thread on /raid/ with an eye-catching thumbnail and title - if you think it will be a long operation with many targets, it is customary to give your thread a title prefixed with "Operation", e.g. Operation Soyclipse, Operation Total Vorefag Death
- Provide as much information in the OP as possible (usernames, accounts, emails, etc.). Just a personal army gif and a xitter screenshot will guarantee a faildox
- /raid/ is sadly a dnb so it is not useful for fastburn raids such as "raid this tranny vtuber's stream" or "send 'za to this literal who I just 'oxxed" - these do better on /soy/
- Collaborate - if your cause is deemed worthy, other /raid/ teens will help you with uncovering more info. Ignore and report derailers. It is a good idea to create a doxtrail (see below) to show the chain of evidence. If you're lucky, an editGOD might make an 'ox video edit for you.
- Windox? - ok great, now you have all the info you need to move onto the next phase
- Deploy to /soy/
- Pre-write your thread in notepad o algo
- Your thread WILL be eye-catching in the 'log. Choose an image and title carefully (omit the actual thread title and use redtext and ALL CAPS at the top of the post body, it's better). Include screenshots with brimstone they posted (censor NSFW)
- Your thread WILL give a short few-sentence summary of who they are and why they deserve 'oxxing. /soy/im respond better to inflammatory and enraging stuff so it doesn't hurt to exaggerate a bit as long as you aren't lying.
- Your thread WILL include usernames, emails, account links, passwords, etc.
- Your thread WILL include a link to the /raid/ thread. This allows /soy/im to check evidence and helps increase activity on /raid/
- Your thread WILL include a nicely-formatted fulldox with the following (* = bare minimum for a windox)
- * Full name (including deadname if applicable)
- * Address(es)
- Phone number(s)
- Date of birth
- Relatives - include contact details (phones, emails, etc.)
- School / College / Workplace - include email to report misconduct
- Tip line for local police (if relevant)
- Your thread WILL include a call to action, e.g. 'OX. 'APE. 'ILL. or 'ZA AND 'MONS NOOOOWWWWWWWW
- ENABLE IDs!!
- If derailcorders appear, DO NOT ENGAGE. Just filter by ID+. Even 'jakking a derailer contributes to derailment.
This is the only correct way to respond to derailcord
- Ruin xeir life - send them a brimmy 'za, send 'mons, scientologists, qurans, and so on. Contact relatives, place of work, etc. and include evidence. Spam 'ox on xeir socials and 'cords.
- Gather seetheralds - This is important. It is a good idea to have at least one subtle slowburn account inside their 'cord server (join before making the /soy/ thread) so you can collect gemmy screenshots of the meltdown to post on /soy/
- Immortalize - Make an article about the operation here on the 'ki if it's a gemerald. If it's SNCA just add to List of doxes. Also add any 'oxxeralds to the table for Operation PRISM.
The Doxtrail[edit | edit source]
A doxtrail is the trail of evidence that you follow in order to find information while doxing. Documenting the doxtrail is essential to prove that your windox is actually the person you say it is. A doxtrail doesn't have to be intimately detailed, but it should be detailed enough that an average soyteen would be able to follow it and find the same results. An example of a doxtrail in which the target's name, address, phone number, and e-mail address were found:
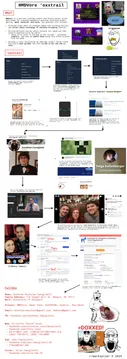
- Searched their username on Swolesome.vip and found a breach that leaked their e-mail address.
- Use a program like Blackbird or Sherlock (or Soylock) to search accounts with the related email or username.
- Looked for other breaches including that e-mail address and discovered their other accounts
- Other accounts revealed their name and approximate location (state, city, county, etc.)
- Searched Addresses.com for their name in that location, found their address and phone number
When your target is made aware of the 'ox, it is very common for them and their 'cord xisters to call the 'ox a falsenvke as a form of damage control. Having a watertight 'oxxtrail will deboonk any of these attempts.
Methods[edit | edit source]

Check for existing doxes[edit | edit source]
Before trying to dox someone you should check if someone else has already done the work for you. Try searching their name or checking dox websites like Doxbin and the 'farms.
Do note the 'ki has central collection of doxes available at Operation PRISM, thoughever it is not complete.
OSINT[edit | edit source]
OSINT is using publicly available information to dox people. This is usually checking everything on someone's social media accounts to find any locations or any real life connections. CIA hires you to do these stuff. CIA does NOT spy on you. This is just a tinfoil hat Chudcel.
You should learn how to program, in a scripting language like Python, for writing simple scripts for automating tasks like searching for usernames.
Mind you some OSINT tools like name search websites and other tools that have public records do not exist in outside of the United States and Canada, The UK has strict regulations and most of their databases comes from 2017 and is not mostly up to date. Make sure to use the OSINT list down in the links section of this article.
Onion Sites/Dark Web[edit | edit source]
Main article: Dark Web
Some onion sites host archives, medical records, data breaches, and more that wouldn't be available on the clearnet. In order to access these you must use a browser that allows you (Tor is the most common browser to use) and have a place to start. A link directory you can use is tor.taxi which is still one of the best. If you want to find some more links, use DarkNetLive or if you're desperate use Reddit. KEEP IN MIND DO NOT PASTE RANDOM LINKS THAT ARE NOT FROM A TRUSTED DIRECTORY AS IT MAY BE A HONEYPOT. The list will go on as you find more websites you can use. You can also use OSINT on the dark web, so here are some tools for you to use on your adventures.
GeoGODing[edit | edit source]
Obviously many people post photos. If they show outside of their house (or even inside) you can most of the time pinpoint the exact location.
To do this look for anything that can be used for identifications like trees, bridges, etc. Then try putting it in Google images' search and see if anything shows up. If that part in the picture is pretty clear and a Google street view car passed by it, Google will show it to you. But sometimes you're doxing a third world nigger, that country some times doesn't have Google services or they are just living in the middle of nowhere and in that case it becomes harder. To now do it, you have to find the country (if they don't tell you, see what hours they are active and guess) of the nigger and more preferably also find what town, district or just what area they live in. After that you should map out what that area would look like from aerial view. Once you did that, go to Google Earth and try to find something. Once you think you have the location, make sure it's the right location and post it on wherever you want. (obviously you don't want to send 'za to a ww2 veteran with PTSD and financial struggles).
There are some tools that claim to be able to geolocate an image using AI. These are usually useless but may work for distinctive locations that have been photographed a lot; they will not help you find the location of a photo of some tranny's back yard.
GeoGOD-specific tools can be found in the links section of this page.
Training[edit | edit source]
This method can be hard if you're not using Google images, so you need some training. You can play a lot of GeoGuessr which will give you the knowledge about certain countries, like what their trash cans look like, if the houses are like a soviet shithole etc. You need to pay them to play it doe. If you a poor ass nigga use OpenGuessr as it is free.
Geoguessr players have many resources for training in case you want to know what telegraph poles look like in the Mokhotlong region of Lesotho o algo.
- https://geotips.net/
- https://www.plonkit.net/guide
- https://docs.google.com/spreadsheets/u/0/d/1UNvkoY-LaktF75nU_cP7-wVRAEvH3fSqVZet20HqxXA/htmlview - massive library of hints
- https://www.reddit.com/r/geoguessr/wiki/index/
You can also check out JoseMonkey on jewtube. He has a lot of videos on geoGODing people consensually.
Emails[edit | edit source]
Emails are extremely valuable during doxing. Access to the emails are a lot more valuable, it's like finding a massive diamond while mining. Emails are usually used when the person knows how to stay anonymous, and most other methods can't be used. Emails are used to gain access to other accounts that could have very sensitive information.
It is always a good idea to feed the email into https://epieos.com/ or ghunt as this can often reveal a google maps profile which can reveal their approximate location if they left reviews. Sometimes they use their real name for the profile too. Also, don't neglect the "Google plus archives" feature in epieos - some uncs did actually use that platform geg.
You should also try searching the first part of the email (before the @) on Soylock and Swolesome.vip as if it were a username (thoughever you can just search "thefirstpart*" and enable wildcards in swolesome to show both usernames and emails). Some sites will use the first part of the email as the username by default. Pinterest does this and will sometimes give you their real name.
Git[edit | edit source]
One of the most underrated datamining methods is going through a user's commit history to find their email address. When you push a commit to sites like GitHub, your email is included in the commit due to the way Git fundamentally works o algo. Unless the target is an opsecGOD, this is basically a 100% guaranteed way to find emails.
To do this, go to any of their repositories and click on a commit hash, then add ".patch" to the URL. You should see their username and email at the very top of the page. If the email is a noreply address, then make sure to look at older commits and alternative sites like GitLab and Codeberg if they have an account there.
Password resetting[edit | edit source]
After getting into the email, you can access almost every other account using the platform's reset password feature. This will alert the target so make sure to immediately delete the message (make sure to remove it from the bin as well)
Databreaches[edit | edit source]
Databreaches not only contain passwords, they might also contain things like IPs and loads of other stuff like phone numbers. Almost all the time you need to buy the databreach file as a .zip that ends up being a retarded file format used in 1488 B.B.C. but you might be able to actually see it if you actually get in contact with the seller.
If you have a password, you might be able to log into the target's email account as most people retards use 1 password for everything.
The best website for free public databreaches is breach.vip, also swolesome.vip (a sharty frontend for breach.vip).
If you want to find databreach pastes, a forum you can use is leakbase.io, and another (most likely an FBI honeypot as it was seized multiple times so please try to avoid it) is BreachForums.st. Use haveibeenpwned.com to see if they're part of a data breach, however some pastes already existing might not be in the pwned database.
Payment Processors (PayPal, etc.)[edit | edit source]
Try just putting their usernames into these URLs:
- https://paypal.me/theirusernamehere
- https://cash.app/$insertusernamehere (geoblocked to the US – use a VPN, be sure to keep the $ before the username)
- https://account.venmo.com/u/insertusernamehere
This will often give you their full name and sometimes their location. Seriously, you would be surprised how often this works, maybe around 30-40% of sharty 'oxxes are found using this method. Be sure to snopes it though if it's not a unique username as it could be some random nophono.
Ko-Fi[edit | edit source]
If they have direct payments with paypal set up on their ko-fi page, you can put in a fake username and email and click "tip". This may reveal their email or name on the next screen.
Facebook stalking[edit | edit source]
Get good at it. Your target might have great OPSEC but their auntie Margaret probably doesn't. If you have a name and general area, use the people search feature to search the target's surname and filter by the town (works better in small towns and for uncommon surnames), then datamine potential relatives (many will have public friends lists so you can map out relations). It is highly likely that there will be a photo of the target on their grandma's page somewhere o algo, which will make the 'ox more impactful as having a photo will scare the target more.
This is also useful for contacting all relatives after the 'ox is confirmed so you can send them all the degenerate activity the target has been involved with online.
Steam account[edit | edit source]
Getting your target's Steam account can be a gemmy find. Sometimes you're lucky and immediately spot past usernames or their location in the profile details. If they have any videos uploaded on their Videos section, you can get their youtube channel. You can also go into profile comments or the Screenshots section for additional clues.
If nothing turns up there, paste the profile URL into SteamHistory.net. This tool reveals old usernames and profile pictures.
"Friend"[edit | edit source]

Some times you might have to use tactics related to that person's life to gain info. This usually works with older people as they almost always have had a crush on the school's cheerleader and they are willing to cheat on their wife of 7 years for her.
Talking with xis mother[edit | edit source]
The person you are doxing most likely has an absent father, and xis mom is also just way more stupid. By talking to her, you can convince her you're a friend from back in school or something and you want to send xim a gift for giving you hope or something or that you just wanna meet up with xim. Xis mother will most likely give you the address and you can send the 'za. You might also be able to offer her BWC and then kidnap and rape and torture her until she leaks the location of the gold she burried with her husband in 2003 then kill her and abuse the corpse. She might have a facebook account and if she does she usually has her whole address, phone number, full legal name, and basically everything about her in there.
Legal action[edit | edit source]
If you decide to take legal action against someone, you will be given access to many many personal information by the government. This is the riskiest way to dox as they might also get access to your personal information. Usually jewtubers use this method when they get exposed, they file a copyright claim and leak the uploader's information online. The other party typically doesn't do the same because of the risk involved. Overall, this is the riskiest but an effective way of doxing if the target is famous.
Talking to xiers school[edit | edit source]
Having the school and first name but not the last or not sure if the name is true, call Xiers School and say, Xier is your sibling o algo and that Xiers is sick and wants to go home. They will check if Xier is in the school's database or whatever they have and tell you if Xier is a student there if the name is true, and if you ask for the last name as confirmation, you're successful.
Spear Phishing[edit | edit source]
Spear phishing (sometimes spelled as one word) is a phishing attack that is targeted at one person. This can be a useful way to gain more information if all you have is the target's e-mail address. If you have their phone number, you can use that to perform vishing (voice phishing) or SMShing (phishing over text message).
The Wayb*ACK* Machine[edit | edit source]
Somehow this hasn't been listed yet despite being easily one of the most effective tools for 'oxxing, especially for furfags and other gooner artists. Niggas did not give a shit about OPSEC in 2009, you can use this to your advantage.
- First, find their accounts. Look for ones that are old as they are more likely to reveal gems.
- Copy the account url and enter it here, or use this browser extension (lets you quickly open a page in various web archives, available for all major browser families)
- NOTE - for tumblr urls, you will usually get older results for e.g. "username.tumblr.com" rather than the default "tumblr.com/username". Same applies to deviantart urls (e.g. "nophono.deviantart.com" rather than "deviantart.com/nophono")
- For youtube channels, you can get older results if you look for the channel with the id on the link, rather than the username (e.g. "youtube.com/channel/UCUESjxU6UjPmVv8h_-ORDVA" rather than "youtube.com/@soyjakpartyvideoarchive"). There are plenty of online tools to get a youtube channel's id.
- Go back in time and datamine their account pages for old usernames, other accounts, emails (yes, it was common to put your personal email on a public page in the 2000s and early 2010s), real names, locations, etc.
- Generally, the older snapshots will have more valuable info but you shouldn't neglect the rest
- If you can find old aliases and emails, they will be much more likely to show up in breaches
Older sites like furaffinity, deviantart, tumblr, etc. are often absolute gem mines.
This method is also keyed because it lets you explore heckin sovlful web 1.0 gemmies o algo ![]()
Searching pruned archives[edit | edit source]
Archive.org is infamous for taking stuff off their archival services, usually due to it containing CSAM and other illegal material (which is a good thing) or due to the account owner requesting it to be taken down (not good for us). This is sometimes an indicator that this person may have been doxed in the past, so be sure to double check.
When you've found an account which should have been archived, but the Wayback Machine says that no archives exists, click the "search for all archived pages". Then you may be able to find archived posts that the account owner haven't requested deletion of, these may reveal useful information outside of the post itself as the archive can contain old aliases, profile pictures, location information and birthdays, especially on Xitter.
URL MIME type search[edit | edit source]
This is more effective against oldGOD personal sites. If you paste in the website root and click "URLs", it will show you every url saved from the site, with a searchbox. You can search for potentially interesting files, e.g. MS Office documents (possible personal info in the metadata), JPEGs (exif scrubbing only became common in the last ~10 yrs so maybe there are GPS tags in photos), source code (maybe leaked API keys o algo if they can't code).
Website domain lookup (whois)[edit | edit source]
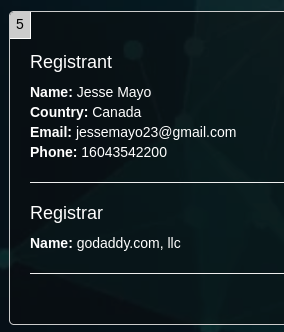
A whois query is a way of finding the registered information of an internet domain or IP address, including it's registrar (the company the domain is registered by) and registrant (the owner of the domain).
A required part of registering a domain for a website or email is providing the registrant's name, contact info, and home address, which can sometimes show up in a whois query if the registrant has opted not to use a domain privacy service (thoughever basically everybaldi uses one now). Whois queries usually return the following information:
- The registrar (The company that the registrant purchased the domain from)
- The registrar's contact information and abuse email (Used for deploying RegistrarNVKEs)
- The registrant's name and contact info (unless redacted by a privacy service)
- When the domain was registered, updated, and expiry date.
- Domain status[1], see notable ones below:
clientHold- The domain has been temporarily suspended, usually due to legal issues, non-payment, or will be deleted in the near future.serverRenewProhibited- The domain is perma 'nished and can never be renewed.pendingDelete- Domain will soon be deleted and purged from the record.
If you're a keyed linuxARYAN, just run whois <DOMAIN NAME HERE> (remember to type just 'nophono.com', not 'https://nophono.com') in your terminal to get the whois info as it comes preinstalled on most distros.[it just does, ok?]
Free web tools also exist for checking the owner of a domain, such as who.is and whoisfreaks.com. Whoisfreaks notably offers a historical whois lookup tool, to check if any gemmy information has been changed or redacted. (Requires an account but just use a burner doey)
You can check the registrar, webhost, and email provider using this all-in-one tool.
NameMC[edit | edit source]
NameMC is a website that lists previous usernames and skins of Minecraft accounts, since Minecraft is a game that literally everyone has played at some point in their life, it's a great method for finding old usernames to later look up in breach databases or to look up other accounts using that same name using the Wayback Machine. Since most targets like to keep their accounts that they played on as kids instead of making new ones.
Business register lookup[edit | edit source]
Since many of the sharty's targets are public figures who make money from some form of self employment (e.g. goonslop producers, game devs, streamers, etc.), they will often have a company registered under their name to collect shekels. Most US states (maybe all) and many other countries (such as the UK) require an address for the company to be registered at, and it must be made public. If you have the target's real name and a rough location (state, country) this makes it easy to search the relevant business registry for their name - you will hopefully find an entry that has documents listing their address. Most will just use their home address to register the company as the alternative requires parting with some shekels to pay for a company registration service.
A lot of the targets are kinda retarded and name their company with their username, so if you don't have their full name, try searching the registry for their screen name. Two major onlygoys whores were 'oxxed using this method during Operation No Nut November.
Most country/state registries are free to browse but some will be paywalled (e.g. Texas and the Netherlands), thoughever it is typically only a couple bucks to look something up.
Voter record lookup[edit | edit source]
The effectiveness of this method varies greatly by state and country as they have different requirements for the level of detail required to view a voter record. For example, Florida only requires a full name and date of birth (this is how the undertroon groomer Shayy a.k.a. Peter Anderson Voss was 'oxxed). However, obsessed Illinois requires a full name, DoB, zip code, street name, and house number, making it effectively useless as you need a fulldox to even view the record. If you get access to a voter record, it will give you their addy (thoughever it may not be up to date as many people don't update it when they move). The UK has this information free to view for any britGOD at their local library, or you can view online for a fee.
VoteRef has the voting records for most US states in an easily searchable database.
Selfies[edit | edit source]
It is possible to reverse image search somebaldi's selfie to find reposts or facial matches. Since google lens got nerfed, there is no good free option for this anymore. Lenso.ai and Pimeyes have a limited free search function, but the urls of matches are paywalled.
There is a possible workaround thoughever - lenso lets you download a watermarked low-res preview of matching images. You can then feed this into google lens and sometimes find the source link. As for Pimeyes, you can search for the url and a keyword in google images to try and find the original. (e.g. site:nophono.com <name of the victim, or something like that yeah>)
Useful accounts cheat sheet[edit | edit source]
When running a username through Soylock (or similar), you will often find a lot of SNCA accounts that don't reveal much. The following list gives some accounts that you should prioritize checking as they often give gemmy info. It is roughly listed in descending order of gemminess. Thoughever, you should check all results if you have time as this list is not exhaustive.
- Paypal - If this appears, check it first. It will often give their full name and sometimes their general location. Also Venmo and CashApp but these are less reliable
- Snapchat - Often gives full name
- Instagram - Sometimes gives full name
- Pinterest - Same as above
- Facebook (Facecuck) - Normally needs full name to find the account, but it holds their general or sometimes even exact location, date of birth, friends, family and usually multiple face portraits. Most effective on older-aged targets because xhey're more likely to have a public account and terrible opsec
- Furaffinity - Since it is an old site and almost every furfag uses it, you can often find gemmies by checking it on the wayback machine. Also InkBunny
- DeviantArt - Same as above. Also usually gives you their birthday
- ArtStation, Freelancer - Often reveals name and general location
- Tumblr - Old site, check wayback machine
- Wordpress - Maybe an old personal website with gemmies
- Laby.net (or use NameMC as Laby seems to be unstable recently) - This shows their 'craft username history and can reveal old usernames to datamine
- Steam (user) - Similar to above, click the arrow by their name to see old usernames. Also can reveal their country and sometimes first name
- Geocaching - This site was very popular in the early 2010s and many users made their geocache finds public, which can give you an idea of their general location (thoughever you need to make an account to view). If you can get into their account, you may see their home address coords in the settings.
- Linktree, Carrd, Straw.page, AllMyLinks, About.me, etc. - Quickly shows you all their socials. If you're lucky, it will be an old page that they forgot to delete and will give you usernames they want to keep hidden. You can also try it in the wayback machine.
- Xitter, jewsky - Usually their main social, you can datamine for info like city, age, etc. When searching the wayback machine, be sure to try their handle on both the x.com domain and twitter.com.
LarpGODing[edit | edit source]
Knowing how to blend in with degenerates is a very valuable skill, as you can often get more info from targets and their associates if they trust you. You should know how to design your profile to look like one of them - first determine what type of people they are (trannies, furfags, pedos, femgoys, etc. - there is a lot of overlap between these groups but there are subtle differences) and adjust your profile accordingly. If in doubt, an anime profile pic blends in pretty much anywhere, but make sure you know the character you use because somebaldi might ask you about it.
Unfortunately, it is quite hard to explain how to be an effective larpGOD as it is mostly a skill you get through observation and some degree of improv ability. It is easier if you were groomed and/or EPI'd at an early age, like most 'teens were.
First, here are some things you SHOULD NOT DO:
- Sharty references, even subtle ones, are a terrible idea. Remember, the sharty is not a sekrit club anymore and many troons know about it (and even browse it)
- Do not join during a raid - you WILL get caught in the ban wave. Ideally join before 'teens raid the server as they usually pause invites after
- Do not immediately start asking for info. Make friends and integrate first
Designing your profile[edit | edit source]
Here are some ideas for your profile pic:
- Anime characters - make sure you know the anime and name of the character
- Furry characters - either get some random nophono's OC from furfagffinity or use a popular character like Loona o algo
- Lain - troons love this because she is literally xem o algo, thoughever it is a little cliche
- Troonslop indie game / show characters - make sure you know a bit about the media itself
- Goykisser - ideal for infiltrating groomcords
- Blahaj - troons are obsessed with this o algo, there is a lot of blahaj art you can use
- 'blox - good if you're larping as a caca
For the name, you have many options. Some ideas are given below:
- Typical tranny names like Luna, Alicia, Lilith, Alice, Vivian, etc.
- Something Japanese - you can use a variant of an anime character's name if you have that character as your pfp
- Fursona-style name - e.g. LunaFoxxy, max_the_husky, KatieKitsune, etc.
For the bio, you can just write some random quirk chungus shit like "Pineapples ^w^" or whatever. Or ideally give some actual details like interests, age, etc. remember you are essentially creating a character here. Troons and furfags often give their age like "Level 16 in life". When infiltrating an actual pedocord, you can give your age like "21 🔄" - this is how a 12 y/o grooming victim would give their age, as the arrows imply to swap the digits.
Typing style[edit | edit source]
Haiiii :3
This is how u type like a furfag ^-^ *nuzzles*
U should also have a TXT file made up of links of cute widdle fops (fox) gifs and furfag reaction images (right click on the image and then press "Copy image address") to post (〃ω〃)
Remember to be extra silly bc furfags are all freakin goobs *boops* :3
U can also repeat the last letter of words like thissss ^w^
Adjust the quirk level to the other users, not all furfags and troons talk like this, but most do.
Using furfag emoticons is a good idea. here is a table of some common ones:
| Emotion / Usage | Emoticons |
|---|---|
| Happy / Friendly / Soft | :3, =3, ^w^, ^_^, UwU, owo, OwO, >w<, ^-^, •w•, (^▽^), (≧◡≦) |
| Playful / Mischievous | ;3, >w>, <w<, :>, :<, x3, ^~^, (¬‿¬), ( ̄ω ̄) |
| Curious / Surprised | owo, OwO, Owo?, o_o, O_O, 0w0, (・o・), (⊙ω⊙) |
| Shy / Embarrassed / Blushing | //w//, >///<, ^///^, (⁄ ⁄•⁄ω⁄•⁄ ⁄), (⁄ ⁄>⁄ ▽ ⁄<⁄ ⁄), (〃ω〃) |
| Sad / Hurt / Whiny | ;w;, ;_;, QwQ, TwT, T_T, u_u, (;ω;), (╥ω╥) |
| Angry / Grumpy | >:[, >:(, òwó, ಠ_ಠ, ( ̄^ ̄), (≖︿≖) |
| Confident / Smug / Teasing | :w, Uw<, >w<, ( ̄︶ ̄), (¬‿¬), (≖ω≖) |
| Excited / Hyper | !w!, OwO!!, ^W^, (ノ◕ヮ◕)ノ*:・゚✧, ≧w≦ |
| Sleepy / Cozy | -ω-, =_=, uωu, (-ω-) zzZ, ( ̄ρ ̄)..zzZZ |
| Affectionate / Comforting | *boops*, *hugs*, *paws at you*, ^w^♡, UwU♡, (つω`。), (づ。◕‿‿◕。)づ |
Getting info[edit | edit source]
Once you have integrated, you can start subtly datamining for more information. Here are some things you can do:
- It is generally acceptable to ask for someone's general location, maybe start by asking for country and/or timezone and they will often give you the state/city as well
- Remember to share your own (fake) information as it makes them more likely to reciprocate
- E.g. "woow i need to sleep it's 3AM here in the UK" may prompt them to tell you what country/tz they are in
- Ask them for other accounts that may not be linked in their profile - e.g. "heyyy @TrannyPedo do u have FA? :3"
- LAST RESORT NVKE - you can ask them for thoughts on your OC (steal one from FA), which you upload to an image sharing site, then create an IP grabber that links to the image (make you choose a grabber link that looks legit)
- This is likely to blow your cover but these niggers are kinda retarded so not always
Confirming the 'ox[edit | edit source]
Sometimes, you will have an 'ox that is likely correct but lacking the final snopes. Here are some methods you can potentially use to confirm it.
Post it[edit | edit source]
Arguably the simplest method, you can just post the 'ox (or part of it) to their 'cord or a social of theirs and gauge their reaction. IMPORTANT: you must post it in a way that would result in no reaction or confusion if it's a faildox, but would prompt them to delete, ban you, and/or sperg out if it is a windox. So don't just spam the entire fulldox, as they would delete these messages even if the 'ox is wrong. Here are some subtle ideas:
- Get a google streetview pic of their suspected house, or interior pics from a real estate site, and post it in the 'cord saying "Just moved in!", or "What color should I paint my walls?" or something similar
- Weave the 'ox into an innocuous sentence. E.g. if you think they live at "14 Nightingale Ave, Akron, OH" you could say something like "14 nightingales just flew past my window. Only in Ohio :skull:"
Scouting the house's layout[edit | edit source]
If your target has previously shared photos taken inside xis/xer home, you can compare those images with interior photos available on real estate sites like Zillow, Realtor, or Redfin to identify potential matches. Always verify that the photos are recent, as your target may have moved, and any addresses obtained from sources like Whitepages could be outdated.
Boots on the ground[edit | edit source]
You can send various things to them and monitor for any kind of reaction when it arrives. These methods are most effective with livestreamers as you can view the live reaction, thoughever, many targets would post their reaction to der 'cord due to an autistic need to share every detail about their lives.
- Send 'za - While it is unfortunate if a nophono gets a 'za due to a faildox, it will only result in a very mild inconvenience for them so it is arguably worth the risk. After delivery, they may send a message about it in der 'cord, but if not, you can bait a reaction by saying something like "@Troon did you enjoy the pizza?" - if it was a failza, they will just be confused. If they ban you, you know it was a winza.
- You can potentially also datamine the 'za delivery driver as follows:
- Order the 'za to the suspected addy
- Include your burner number in the order form
- When the 'za is inevitably rejected, call the delivery driver and say something like "Hey man did my order get rejected? I think my brother/mom/sister might have answered the door - what did they look like?"
- Hopefully, the driver gives a matching description of the target
- You can potentially also datamine the 'za delivery driver as follows:
- Order a taxi - You can call for a cab to their address and tell the driver to sound the horn when they arrive (good for livestreamers)
Help with doxing[edit | edit source]
These methods aren't just all. You most of the time will need some other methods to be able to use those main methods. These just vary on the person and there isn't a method to use for everyone but they still work well. You can always ask the Sharty for help. Remember Sharty is always your personal army.
Video tutorials[edit | edit source]
Your friendly Indian 'oxxing guide, 1337_p4j337, has kindly made some video tutorials on 'oxxing for nusois.
Linux distro used in these two videos if anyphono wants to know: endeavourOS w/ KDE (on a vm)
Dox-alongs[edit | edit source]
-
Episode 1: nebulanursery
Specific guides[edit | edit source]
-
Sending 'za
Links[edit | edit source]
Some of these come from a /raid/ post that was called the same thing. Newer archive. You WILL help to expand it.
Meta-lists and guides[edit | edit source]
- https://fmhy.net/internet-tools#osint-collections - has a lot more than this list
- https://doxbin.com - Dox repository
- https://start.me/p/L1rEYQ/osint4all - Tools list
- https://start.me/p/aLe0vp/osint-resources-in-canada (OSINT resources for Canada)
- https://anonpaste.io/share/0b00ed50a9 - Tools list
- https://osint.rocks/ - collection of command line OSINT tools that you can run in the browser
- https://uk-osint.net/index.html - UK-focused
- https://lambda.black/osint.html - OSINT site with tag system for multiple tools
- https://github.com/jivoi/awesome-osint
- https://docs.google.com/spreadsheets/d/18rtqh8EG2q1xBo2cLNyhIDuK9jrPGwYr9DI2UncoqJQ/edit?gid=930747607#gid=1575012979
- https://web.archive.org/web/20210426041234/https://jakecreps.com/tag/osint-tools/
- https://github.com/apurvsinghgautam/dark-web-osint-tools - Dark web OSINT
- https://doxbin.com/upload/howtodoEVERYTHINGYOUNEEDTOKNOW
- https://doxbin.com/upload/DOXXING20GUIDE
- https://soyjakwiki.org/File:How_to_dox_pedophiles_slash_bad_people_educational_video.mp4
'chiving - Please do this[edit | edit source]
Main article: Archiving
- https://github.com/Tyrrrz/DiscordChatExporter - Discord chat dataminer
- https://github.com/bbolli/tumblr-utils - scrape tumblr blogs including login-only ones
- https://github.com/Serene-Arc/bulk-downloader-for-reddit - reddit bulk downloader, can fetch all posts for a particular user
- https://preservetube.com/ - 'chives jewtube videos and channels
- https://megalodon.jp/ - archive webpages (ZOMG IT'S JUST LIKE MY FAVORITE ANIMES)
- https://archive.ph/ - like above but unstable and
might be ACKed soonhas been running for like 10+ years now (the unstable part is true doe) - https://web.archive.org/ - The largest web archive by a long shot, but it's run by selfish little fucks who blacklist anything they don't like, so don't use it as your only archive.
Breach searching[edit | edit source]
- https://dox.soy/ - A sharty themed breach database run by SurrealSec, who also operate ███.███ and gem.soy, has a wider selection of breaches than swolesome and breach.vip[it just does, ok??] (thoughever breach/swolesome have some breaches that dox.soy does not, you should use both)
- https://swolesome.pages.dev/ - swolesome.vip, a sharty-created improved frontend for breach.vip (still in beta)
- https://breach.vip/ - Free and requires no signup, just use swolesome doe since it's le keyed
- https://oathnet.org/ - Breach lookup, has more than breach.vip but requires registration
- https://t.me/kyanitepw - Paid telegram breach search bot. Can pay in rubles or robux. Use with caution as one 'teen got banned for being in one of their 'cords or something
- @Datawave - could be an alternative to the above
- https://snusbase.com/ - Paid breach lookup
- https://idleakcheck.com - Search leaked IDs including SSNs. Requires registration
Username/email datamining[edit | edit source]
- https://github.com/sherlock-project/sherlock (you should use the sharty version Soylock - https://github.com/SystemCallW/Soylock, since sherlock gives a thrembillion false positives)
- https://github.com/p1ngul1n0/blackbird
- https://whatsmyname.app/ - if you don't want to install anything
- https://epieos.com/ - great for checking if an email has an associated google maps account
- https://github.com/mxrch/GHunt - finds google maps accounts linked to an email, and can get an email from google drive links
- https://osint.sx/ - similar to sherlock, but paid. tells you what apps/websites an email is signed up to and all their profile info
- https://intelbase.is/ - free alternative to above
- https://github.com/Malfrats/xeuledoc - reveals the email of the creator of any jewgle doc, even if they hid their details[a]
- https://github.com/megadose/holehe - checks where an email has been used to register an account. thoughever it is an abandoned project and does not work for a lot of the sites it checks now. Make sure to install via "git clone" and not pip because the pip version is even more outdated.
People search[edit | edit source]
- https://www.whitepages.com/ - the go-to for US targets
- https://www.truepeoplesearch.com/
- https://www.officialusa.com/
- https://www.searchpeoplefree.com/
- https://www.192.com/people/ - for UK targets, much of the info is paywalled thoughever
- https://whitepagescanada.ca/ (Provides more accurate results for Canadian doxes since 411Canada can sometimes hide someone's name)
- @taydhrhvwjaide_bot - Telegram bot for searching for Russians
- https://www.countyoffice.org/ - allows you to check property owner of an address
- https://www.118000.fr/ - for French targets
GeoGODing[edit | edit source]
- Map providers: Google Earth, Google Maps, BING, Apple Maps, ESRI, OpenStreetMap (actually has a crazy amount of data)
- Street-level imagery providers: Google StreetView, Apple Maps (much better coverage in Germany than google), https://www.mapillary.com/ (crowdsourced, often 3rd world quality but can be useful for filling in StreetView gaps)
- https://overpass-turbo.eu/ - lets you run geographic queries against the OpenStreetMap database, so e.g. if you have a photo with a picnic bench in a park by a railway line you can create a query to find that. Unfortunately the query language is somewhat of a margerald. Refer to https://wiki.openstreetmap.org/wiki/Overpass_API/Overpass_API_by_Example
H4xx1ng[edit | edit source]
- https://github.com/quasar/Quasar/releases/tag/v1.4.1 - RAT (Remote Access Tool/Trojan)
Post-dox[edit | edit source]
Main article: Minor inconvenience
Main article: Major inconvenience
- https://www.shitexpress.com/ - Mail a box of shit
- https://confettimailbomb.com/ - Mail troll items like a glitter bomb
- https://www.ruindays.com/ - Mail even more troll items like a dickhead trophy
- https://mailbait.info/run - Email spam
Other[edit | edit source]
- https://anonymousplanet.org/ - A very long and comprehensive schizo guide about how to stay anonymous on the internet
- https://www.iplocation.net/ - IP geolocation (it is not pinpoint accurate but can give you an idea of region)
- https://www.faxvin.com/ - A site that looks up license plate numbers in the US
- https://chromewebstore.google.com/detail/blur-the-image-and-video/aikjogmpaoaookmacnkbenekcnkjlkmi - Blurs page content; proves to be useful whilst doxing NSFW artists.
Notes
- ↑ If you have accessed the doc while logged in, you can view the target's email via Google Drive from either Home or "Shared with me". This, perhaps, still works even if the target published it to the web.
Snopes
|
The Ultimate Doxing Guide is part of a series on Computing |
|
LOW LEVEL |
|
|
HIGH LEVEL |
Java • Go • PHP • Python • SQL • Bash • JavaScript • PowerShell • ActionScript • Scratch • Ruby • Lua |
|
MARKUP |
|
|
IMAGEBOARDS |
nusoi • Vichan • Yotsuba • OpenYotsuba |
|
OS |
|
|
MISC |
Babybot • McChallenge • Systemd • MS Paint • JS Paint • Photoshop • Flash • IRC • Ad blocking • Dark Web |
|
AI |
ChatGPT • Gemini • Grok • Vibe coding • Generative AI • Stable Diffusion |




