Current mission: go through Category:ESL and fix the ESL or remove the template if the page isn't ESL anymore.
Steganography

 |
You can read this for more info about the topic |
 |
|---|
Steganography (also called Soyganography) is the practice of sharing an image that holds a concealed image, message, or icon, inside. This can mean hiding a soyjak in the corner of a regular image or flashing cheese in a seemingly static gif, also known as Stealthjakking. Another form of steganography, not visible to the "naked eye", is using special software to embed extra images or messages in the file contents of shared images that only people with the same software tools can see.
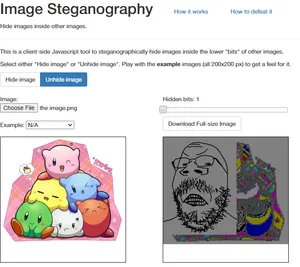
Image embedding[edit | edit source]
Useful for stealthjaking in a way that is so pointless that nobody will probably ever figure out they have been tricked into saving a gem on their hard disk. This is great if you want to spread your gems far and wide when you know an unsuspecting tranny is sharing and spreading your 'jaks across the Internet.
Steganography on imageboards has evolved from simple file padding tricks into more sophisticated methods that slip past automated filters. Instead users now rely on modern tools and formats that can disguise additional data inside otherwise ordinary-looking images.
Some of the more recent approaches include:
- Steghide – A command-line utility that can embed arbitrary files inside JPEG or BMP images with optional password protection. Commonly paired with Stegseek for cracking.
- zsteg – Detects and manipulates hidden data inside PNG and BMP images at the pixel level (LSB steganography).
- OpenStego – A cross-platform Java tool for embedding text or files.
- Custom scripts and browser extensions – While older extensions like Third Eye and P.E.E. have been filtered out, new lightweight scripts appear periodically, often shared privately to avoid detection.
- File concatenation / polyglot files – Hiding other file types (ZIPs, audio, or even another image) appended after the image’s normal end marker (e.g.
IENDfor PNG). Tools likebinwalkcan reveal these.
These techniques allow for stealthjaks where a seemingly harmless image hides another jak, catchphrase, or even a whole folder of gems.
[edit | edit source]
If you suspect an image has embedded content either a gem or coal, there are a few common methods to try:
- Check the file structure – Images like PNG and JPEG have clear end markers (e.g.
IENDfor PNG,FFD9for JPEG). Anything after that may be hidden. Tools likexxdorhexdumpcan reveal suspicious extra data at the file's end. - Use metadata and extraction tools – Run
exiftoolto inspect hidden comments or tags. Usebinwalk -e file.pngto search for and extract embedded files inside an image. - Detect common steganography formats –
zsteg file.pngcan uncover data in PNG and BMP pixel channels.stegdetect file.jpgscans JPEGs for stego signatures.stegseek file.jpgattempts to crack hiddensteghidedata if a password was used.
- Statistical analysis – Tools like StegExpose can flag anomalies in pixel distributions which may suggest LSB (least significant bit) embedding.
If you are not an LinuxGOD doe, there is an simple website you can find called Image Steganography that does LSB encoding.
These methods won’t always work, since some embed tools use encryption or uncommon algorithms, but they cover the most widespread techniques normally seen on forums and imageboards. Be careful with this though as the image may contain actual 'P and which case must be imminently deleted from your hard drive and reported.